Browser Hijackers And The Internet Connection
In the dynamic and interconnected landscape of the internet, the pursuit of seamless online experiences often collides with digital threats lurking in the shadows. Browser hijackers stand out among these virtual foes as a particularly dangerous threat since they sneakily invade our web browsing habits and cause havoc and suffering in their wake. Concerns about online security, privacy invasions, and the overall integrity of one’s digital interactions have been sparked by the continual emergence of these pernicious entities.
Quick Links
Browser hijackers have become a well-known menace that can severely harm consumers’ online experiences. The unnerving capability of these rogue programs to take over web browsers and dictate user choices without permission or agreement is unsettling. This type of interference can take many different forms, such as forcing users to change their default homepages and rerouting their search engine results to questionable websites. The once-familiar terrain of the internet becomes distorted, leading to frustration, diminished productivity, and a palpable sense of violation.
In the face of this escalating predicament, an essential realization emerges: knowledge is power. Understanding the modus operandi of browser hijackers becomes a crucial shield against their disruptive endeavours. Users must be equipped with the awareness of their existence and the tools to combat them effectively. The need for adept removal methods is more pressing than ever before.
Without a doubt, the urgency to comprehend and counteract browser hijackers is paramount. This article acts as a thorough reference, enabling you to confidently negotiate the dangerous waters of digital security. You will set out on a trip to protect your online pages or any websites by learning how to recognize the signs and effects of browser hijacker infections and using effective removal techniques. It lays the groundwork for a safer and more unhindered digital journey by highlighting the dangers these hijackers bring and providing practical remedies.
Understanding Browser Hijackers
Knowledge is the first line of defense against the always-changing strategies of digital enemies in the complex world of cybersecurity. Among the most cunning adversaries, browser hijackers emerge as a particularly crafty and disruptive class of malware. An essential knowledge of these sneaky hijackers’ nature and motivations becomes necessary for a successful defense against them.

Defining Browser Hijackers and Their Intricacies
A browser hijacker, in essence, is a type of malicious software designed with the explicit intent of altering a user’s web browser settings without their consent or awareness. This manipulation might involve a variety of adjustments, such as switching the site’s homepage settings or even choosing which new tabs to open. Unlike viruses or worms that might wreak havoc on an entire system, browser hijackers pinpoint and infiltrate the very conduits through which users interact with the online world—their web browsers.
The Mechanics of Browser Hijacking
An innovative system that cunningly seizes control of a user’s browsing experience is at the core of browser hijacking. This takeover often begins innocuously, with users unknowingly installing seemingly harmless software, browser extensions, or plugins. Unbeknownst to them, these installations carry concealed payloads that surreptitiously modify browser settings. As a result, visitors are frequently diverted to unknown search engines, deluged with endless pop-up adverts, or sent to websites they had no intention of visiting. The arrogance of browser hijackers is shown by this violation of a user’s control over their browsing choices and the altering of their online environment.
Motives Behind Browser Hijacking
The motives driving browser hijackers are as diverse as they are malicious. Foremost among them is the pursuit of monetary gain through advertising revenue. By forcibly redirecting users to specific websites or inundating them with intrusive ads, hijackers generate income through pay-per-click schemes. Browser hijackers also act as channels for gathering user data, including surfing patterns and personal information—an important resource in the world of cybercrime—in addition to their financial motivation. Additionally, certain hijackers are used to advertise particular websites, artificially boosting their traffic and prominence.
In summary, comprehending the workings and motivations of browser hijackers reveals a world where personal autonomy is under attack, with far-reaching repercussions. Users can prevent their digital experiences and sensitive information from falling into the hands of these crafty adversaries by taking proactive measures after getting insight into their activities.
Types of Browser Hijackers
The field of cybersecurity is filled with intricacies, and within its complicated web, browser hijackers appear in various shapes, each with its own mode of operation and effects. One must go into the various categories of browser hijackers that covertly influence and undercut consumers’ online experiences in order to fully understand the range of these unwanted entities.
Homepage Hijackers: A Subtle Takeover

Homepage hijackers, as the name suggests, revolve around the manipulation of a user’s default homepage. Once installed, these hijackers surreptitiously alter the homepage setting of a user’s browser, leading them to a different website upon launching the browser. Without the user’s knowledge, this frequently happens, sending them to a website that might have offensive material, ads, or even harmful software.
Search Engine Hijackers

Search engine hijackers target the very core of online exploration—the search engine. They coerce browsers to use a different search engine than the user’s preference, redirecting all search queries through a predetermined engine. This strategy may produce inaccurate search results, expose users to misleading adverts, and cause annoyance by preventing them from seeing actual search results.
New Tab Hijackers

New tab hijackers intervene when users open a new tab in their browser, redefining their starting point for internet browsing. Users’ intentions and autonomy over their surfing choices are regularly subverted by these hijackers, who frequently direct users to a particular website, page, or search engine.
Examples Illustrating the Diversity of Browser Hijackers
The ecosystem of browser hijackers is as varied as it is pernicious. Examples include the infamous hijacker “CoolWebSearch”, which changes users’ homepage settings forcibly, reroutes searches and tracks user behaviour for nefarious purposes. “Conduit Search” is infamous for redirecting search queries to its own search engine, thus manipulating search results. “Ask Toolbar” once epitomized the concept of bloatware, bundling itself with seemingly benign software and effectively changing browsers’ default search engines and homepages.
These incidents just scratch the surface of the innumerable browser hijackers that are active online, all of which aim to covertly violate users’ digital sovereignty. Users are more equipped to spot indicators of hijacking when they are aware of the subtleties of these categories and the examples that go with them, which allows them to act quickly and appropriately. Users may strengthen their defences and recover their online experiences from these sly foes by remaining knowledgeable about the various strategies used by browser hijackers.
Signs and Symptoms of Browser Hijacking: Decoding the Clues to Intrusion
In the modern world where browsing is a ubiquitous activity, browser hijackers lay in wait, poised to disrupt and manipulate users’ online interactions. Identifying the signs of a browser hijacker infection is paramount to promptly neutralizing its impact and safeguarding one’s virtual sanctum. Let’s delve into the distinct symptoms that unveil the presence of these unwelcome interlopers.

Elaborating on Common Signs of Browser Hijacker Infection
Browser hijackers leave a trail of digital breadcrumbs that, when deciphered, unravel their intrusive presence. Among the most prevalent indicators is an altered homepage. Suddenly, finding your homepage changed to a different website, one that you didn’t choose, is a classic sign of hijacking. Likewise, discovering that your trusted search engine has been replaced by an unfamiliar one is a red flag. This not only disrupts your search habits but also exposes you to manipulated search results.
The plague of unwanted pop-up ads represents another unmistakable symptom. These intrusive advertisements might appear seemingly out of nowhere, interrupting your browsing and disrupting your flow. Such incessant pop-ups, often showcasing questionable content or products, can tarnish the online experience and disrupt your focus.
Potential Security Risks Lurking Behind Browser Hijackers
Browser hijackers not only cause immediate irritation but also a number of security flaws. The simple act of altering your browser settings gives away how sneaky they are. Once established, they may compromise your privacy by disclosing your private and sensitive information to outside parties. They may impose redirects that take you to harmful websites, putting you at risk for phishing scams, malware downloads, and other online dangers.
Additionally, the incessant stream of pop-up ads could harbour malware or lead you to fraudulent websites that aim to extract financial or personal information. In effect, browser hijackers turn the web environment you’re browsing in into a digital minefield where each click carries a risk.
The sum of these warning flags and the related security hazards provides a persuasive picture of the dangers that browser hijackers pose. Users who are able to identify these indicators are better equipped to act right away, looking for ways to get rid of the hijacker and bolster their defences. Users can recover their online experiences from the grasps of unwanted manipulation by remaining watchful and tuned in to the minor disturbances these intruders bring.
The Dangers of Browser Hijackers
Beneath the surface allure of the digital world, where seamless connectivity and boundless information beckon, a dark underbelly festers—one inhabited by the treacherous entities known as browser hijackers. These ostensibly innocent apps have far-reaching effects that go beyond irritation and pose serious concerns to users’ internet security, privacy, and even personal integrity.
Exploring the Menacing Realm of Browser Hijacker Risks
The perils posed by browser hijackers delve into a sinister tapestry woven from multiple threads. Foremost among these threats is the chilling potential for identity theft. Cybercriminals might use sensitive data collected by browser hijackers, which covertly track users’ online activity, to pose as victims or launch targeted assaults. Stolen personal information, such as login credentials, credit card numbers, or social security numbers, can easily slip into the wrong hands with just one click.
The threat of data breaches is also quite real. Hijackers that infiltrate browsers often compromise the security of the data transmitted between the user and websites. Private papers, financial transactions, and private chats could be made available to hackers as a result of this breach, who might use it for their own nefarious ends.
The dissemination of malicious content is included in the danger landscape. Browser hijackers may redirect users to websites laden with malware, unleashing viruses, Trojans, ransomware, or spyware upon unsuspecting victims. This potential infection pathway has the potential to have disastrous effects, including irreparable data loss, system compromise, and financial loss.
Real-Life Instances: The Harsh Reality of Browser Hijacker Exploits
The headlines bear witness to the real-world havoc that browser hijackers can wreak. The infamous “Superfish” incident in 2015 exemplified how pre-installed browser hijackers on certain Lenovo laptops exposed users to vulnerabilities, potentially allowing cybercriminals to intercept sensitive data.
Additionally, the “Fireball” hijacker infected more than 250 million computers globally, converting them into a sizable botnet network that could carry out sophisticated cyberattacks. These instances highlight the widespread effects of browser hijackers, their ability to undermine digital ecosystems, and the pressing requirement for users to strengthen their online defences.
These actual occurrences serve as cautionary stories, emphasizing how vital it is to comprehend the dangers posed by browser hijackers. These hijackers can subject customers to a whirlwind of identity theft, data breaches, and exposure to harmful elements, which goes beyond simple inconvenience. With this knowledge, users may take a proactive approach, putting strong security measures in place and looking for efficient removal techniques to fend off the looming threat of browser hijacker attacks.
Methods of Browser Hijacker Infiltration
Browser hijackers are one of the most pernicious characters in the shadowy world of cyber dangers, which is a tapestry woven with clever strategies. One must examine the various strategies these digital criminals use to infiltrate unwary machines if they are to be understood in the whole context of their infiltration. From cunning software bundling to the manipulation of human psychology, browser hijackers leave no stone unturned in their quest for control.
 Software Bundling
Software Bundling
One of the most prevalent tactics embraced by browser hijackers is software bundling. In this approach, hijackers install genuine software while hiding inside of seemingly innocent programs. Unsuspecting users eager to download a desired application inadvertently invite the hijacker into their systems. This strategy takes advantage of consumers’ confidence in reliable sources by turning the process of downloading software into a possible entry point for malware.
 Malicious Downloads: The Trojan’s Arrival
Malicious Downloads: The Trojan’s Arrival
Malicious downloads, which are frequently disguised as legitimate files, provide browser hijackers with yet another entry point into computers. A simple click on a fraudulent link or a seemingly benign attachment can trigger a chain reaction, leading to the silent installation of hijacking software. These downloads take advantage of consumers’ natural curiosity by drawing them into a virtual maze that threatens their online security.
 Social Engineering
Social Engineering
Browser hijackers are adept at exploiting a vulnerability even the most advanced security software cannot protect against—the human psyche. Through techniques of social engineering, hijackers craft enticing messages, appeals, or offers that manipulate users’ emotions, curiosity, or fear. By invoking a sense of urgency or promising enticing rewards, hijackers entice users to unknowingly download or click on links that deliver their digital payload.
 Unintentional Invitation
Unintentional Invitation
Unbeknownst to many users, the seeds of browser hijacking are often sown through unsafe online practices. Ignorance of basic cybersecurity protocols, such as neglecting to verify the authenticity of downloaded files or failing to update security software, can inadvertently invite hijackers in. Visiting questionable websites, clicking on unverified links, and downloading software from untrusted sources increase the risk manifold. In this interconnected age, where every click and download has consequences, neglecting to adopt safe online practices is akin to leaving the door ajar for virtual intruders.
Understanding the tactics behind browser hijacker infiltration is pivotal to fortifying one’s digital fortress. Vigilance against software bundling, discretion while downloading, and a healthy scepticism towards emotionally charged messages are the first steps towards evading their clutches. Users can reduce the possibility of unintentionally extending an open invitation to the unwelcome presence of browser hijackers by arming themselves with awareness of these strategies and developing secure online practices.
Manual Removal of Browser Hijackers
When the digital realm faces intrusion by the stealthy forces of browser hijackers, users often seek to reclaim control through hands-on measures. The manual removal of these intruders involves a systematic approach tailored to different web browsers. With clear instructions and illustrative screenshots, users can confidently navigate the process and restore their online experience to its unadulterated state.
Step-by-Step Guide to Manual Removal of Browser Hijackers
 Google Chrome
Google Chrome
1: Open Chrome and click on the three vertical dots in the top-right corner.
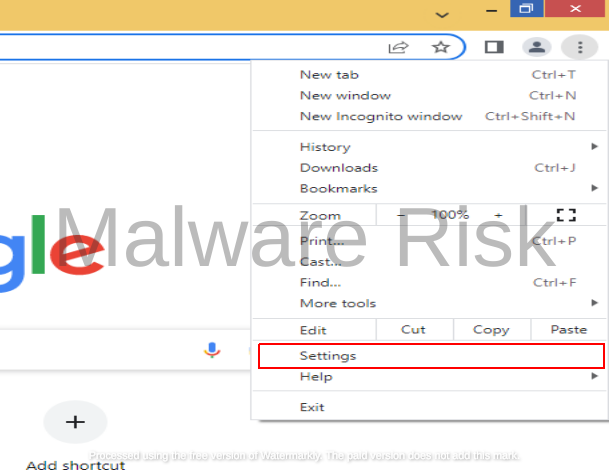
2: Navigate to “Settings” and scroll down to “On startup.”

3: Select “Open a specific page or set of pages” and click “Add a new page.”

4: Remove any unfamiliar or unwanted URLs and save changes.
 Mozilla Firefox
Mozilla Firefox
1: Launch Firefox and click on the three horizontal lines in the top-right corner.

2: Go to “Settings” and select “Home” on the left sidebar.

3: Under “Homepage and new windows,” choose “Custom URL” and remove any unwanted URLs.

 Microsoft Edge
Microsoft Edge
1: Open Edge and click on the three horizontal dots in the top-right corner.

2: Go to “Settings” and scroll down to “Open Microsoft Edge With.”

3: Choose “A specific page or pages” and click “Add a new page.”

4: Remove any unfamiliar URLs and save changes.
 Internet Explorer
Internet Explorer
1: Open Internet Explorer and click on the gear icon in the top-right corner.
![]()
2: Go to “Internet Options” and navigate to the “General” tab.

3: Under “Home page,” remove any unwanted URLs and click “Apply.”

Illustrative Screenshots for User-Friendly Removal
Accompanying each step with illustrative screenshots enhances the user-friendliness of the removal process. Users may visually verify that they are acting appropriately, which reduces doubt and increases confidence. For users to follow, screenshots of browser settings, highlighted URLs and removal procedures are provided.
Users are given the tools necessary to restore control of their browsers through the manual uninstallation process. By adhering to the step-by-step instructions and leveraging the visual aids, users can evict browser hijackers from their digital realm, reinstating their preferred browsing settings. Manual removal is an empowering approach that puts people back in control of their digital adventures in the quest for a spotless online environment.
Using Antivirus and Anti-Malware Software
In the intricate dance between users and the myriad threats lurking in the digital realm, antivirus and anti-malware software emerge as indispensable partners. These technical protectors take up the mantle of defence, using cutting-edge algorithms and heuristics to recognize and eliminate the nefarious threat posed by browser hijackers. They play a crucial defensive role against this invasive threat by detecting them, stopping them, and driving them away.
Identifying and Removing Browser Hijackers
Antivirus and anti-malware tools serve as vigilant sentinels, relentlessly scanning files, applications, and browser settings for any telltale signs of browser hijackers. These programs can quickly detect even the most subtle versions of hijacking software by utilizing enormous databases of known malware signatures, behavioural analysis, and heuristic algorithms. Once found, they quarantine or eliminate the harmful components to stop them from spreading and protect consumers’ surfing experiences.
Comparing Security Software Options
Numerous antivirus and anti-malware programs, each with its own special features and skills to combat browser hijackers, are swarming the digital battlefield. Real-time protection against hijacking attempts is provided by Norton Antivirus, which is renowned for its thorough threat identification. Bitdefender, on the other hand, is lauded for its minimal system impact and effective web protection, ideal for thwarting hijackers’ entry points.
Malwarebytes, a specialized anti-malware tool, excels in detecting potentially unwanted programs (PUPs) often bundled with browser hijackers. It employs advanced heuristics to identify hijacker-related behaviours, making it a stalwart companion in the fight against such threats. AdwCleaner targets browser hijackers specifically, rapidly scanning and purging hijackers from browsers’ intricate nooks and crannies.
Windows Defender, baked into the Windows operating system, offers baseline protection against browser hijackers but may lack the advanced features of dedicated security suites.
Users must consider real-time protection, system impact, user-friendliness, and compatibility with their favourite browsers while choosing security software. Users may customize their protection tactics thanks to the variety of options, strengthening their digital domains against the enduring threat posed by browser hijackers.
In the complex tango between users and cyber threats, antivirus and anti-malware tools orchestrate the defence. They serve as deterrents to browser hijackers, giving users a sense of security as well as useful tools to regain control over their online experiences. Users can confidently navigate the digital world by effectively utilizing these tools because they will be protected from browser hijackers during their online explorations.
Preventing Browser Hijacker Infections
Users must take proactive measures to protect themselves online as they navigate the vastness of the internet due to the lurking threat of browser hijackers. Vigilance and prudent behaviour serve as the defence against these sneaky intruders. Users can build a strong defence against browser hijacker infections by implementing a comprehensive set of preventive measures, protecting their digital space from invasion and manipulation.
A Comprehensive Guide to Prevention
Safe Browsing Habits: Cultivating safe browsing habits is the first line of defense. Verify the authenticity of websites before clicking on links, and avoid suspicious sites that offer too-good-to-be-true deals or downloads.
Avoid Suspicious Downloads: Refrain from downloading software or files from untrusted sources. Stick to reputable platforms and official websites to minimize the risk of inadvertently inviting hijackers.
Keep Software Updated: Regularly updating your operating system, browsers, and security software is pivotal. These updates often contain patches that address vulnerabilities, reducing the potential entry points for hijackers.
Beware of Email Attachments and Links: Be cautious when opening email attachments or clicking on links, especially from unknown senders. Phishing emails can be vehicles for browser hijackers.
Use Strong, Varied Passwords: Strengthen your defenses by using unique and complex passwords for different accounts. This minimizes the risk of unauthorized access, which could result in browser settings being manipulated.
The Importance of Regular System Maintenance and Security Audits
Regular system maintenance is akin to maintaining the locks on your digital doors. Run frequent scans with reputable antivirus and anti-malware software to catch and remove potential threats. By conducting security audits, you can find and fix any potential vulnerabilities that might have slipped in unnoticed by evaluating your browsing history, installed extensions, and software.
Users can actively protect themselves from the unsettling possibility of browser hijacker infections by taking these preventive measures. The digital landscape need not be a treacherous maze; with prudence and awareness, users can traverse it confidently, secure in the knowledge that their digital experience remains untainted by the manipulative tactics of browser hijackers.
Conclusion
Browser hijackers are a sobering reminder of the vulnerability of our online pages and websites in the vast tapestry of the digital age, where exploration and connectivity go side-by-side. The journey from curiosity to comprehension, from vulnerability to vigilance, is a task that users embark upon to reclaim their digital sovereignty.
The battle against browser hijackers transcends mere inconvenience; it is a quest to safeguard not only our data and privacy but also the integrity of our online experiences. As we traverse the intricate network of websites and applications, we must embrace safe browsing habits and judicious downloading practices. The vigilance to recognize suspicious emails and the diligence to maintain updated software form the keystones of our fortifications.
Regular system maintenance and security audits are the things that guard our digital gates, ensuring that no lurking vulnerabilities grant passage to these hijackers. Our choices in password protection, our discernment in email interactions, and our commitment to responsible browsing collectively create a formidable barrier against the intrusion of browser hijackers. If you notice something wrong in the steps or article, Click here to suggest an edit.

Nishant Verma is a senior web developer who love to share his knowledge about Linux, SysAdmin, and more other web handlers. Currently, he loves to write as content contributor for ServoNode and also collaborated with MRLabs now.

