In a world increasingly reliant on digital platforms, maintaining the health of your PC is essential. Malware, a common threat to both individual and corporate systems, is an umbrella term for various malicious programs designed to compromise your data’s security, privacy, or performance. This comprehensive guide aims to demystify malware types, exploring how they infiltrate Windows systems. Furthermore, the guide will illuminate ways to use Windows Defender – an effective, in-built anti-malware tool. Recognizing that additional protection layers can significantly enhance system security, we’ll also delve into reliable third-party anti-malware tools. Finally, preventive measures shouldn’t be underestimated – we’ll equip you with knowledge about safe online habits, importance of system updates, and utilization of firewall technology to minimize malware infection risk.
Quick Links
Understanding The Malware
What is Malware?
Malware, short for malicious software, refers to various forms of harmful software designed to infiltrate, damage, or disable computers, computer systems, networks, or even steal personal information. It is a broad term that encompasses various harmful and intrusive software including viruses, worms, trojans, ransomware, spyware, and adware.
Different Types of Malware
- Viruses are self-replicating malware that spread by inserting copies of themselves into other computer programs or files.
- Worms are standalone malware that spread across networks without the need for a host program or human help.
- Trojan horse malware disguise themselves as legitimate software but upon installation, they can take control of your computer.
- Ransomware locks you out of your files and demands ransom to unlock them.
- Spyware stealthily monitors your computing activity and sends the data back to the malware originator.
- Adware serves unwanted ads and can also come with spyware capabilities to gather data about your surfing habits.
Malware Infection on Windows Systems
Malware usually finds its way onto a Windows system through the internet and emails, often disguised as a legitimate software download or a clickable link. Sometimes it comes bundled with free software from the internet or may spread via removable drives, such as USB drives.
For example, a virus can be attached to an email sent from an infected computer, be disguised within free-to-download music, a game, or a torrent file. The virus then replicates and inserts itself onto other systems every time the contaminated file is shared.
Trojans can trick users into loading and executing them on their systems. Often, the user is duped into believing that the Trojan is a useful piece of software.
Malware can also exploit security holes in a network to access a computer without the user’s knowledge. A worm, for example, can exploit security vulnerabilities to spread itself automatically to other computers through networks.
Potential Impact of Malware
The potential impact of malware on a Windows system varies extensively depending on the type of malware. Generally, it can slow down your system, corrupt or delete your files, change your system settings, or even control your computer. Financial and identity thefts are also common goals of malware. In some cases, an infected computer can be turned into a bot to spread malware or launch attacks on other systems or networks.
Using Windows Defender
All About Windows Defender
Windows Defender is a comprehensive anti-malware component of Microsoft Windows. It is designed to detect and remove malicious software (malware), including spyware. This tool provides real-time detection and removal of malware threats using various methods.
Running a Quick Scan With Windows Defender
To use Windows Defender, you need to run a malware scan on your Computer. Here is how to run a Quick scan:

- Click the ‘Start’ button and type ‘Windows Security’ into the search bar, then click on it.
- Click on ‘Virus & Threat Protection’.
- Under Current Threats, click on the ‘Quick Scan’ button. This scan will check the areas on your computer that malware is most likely to infect.
Running a Full Scan With Windows Defender
A full scan checks all files on your disks and all currently running programs. Here’s how to run a Full scan:

- Click the ‘Start’ button and type ‘Windows Security’ into the search bar, then click on it.
- Click on ‘Virus & Threat Protection’.
- Under Current Threats, click on ‘Scan Options’.
- Check the button next to ‘Full Scan’ and then click ‘Scan Now’.
This process might take much longer than the Quick Scan, hence ensure your Computer is plugged into a power source.
Running a Custom Scan With Windows Defender
A Custom scan allows you to scan only the files and directories that you choose. Here’s how to perform a Custom scan:

- Click the ‘Start’ button and type ‘Windows Security’ into the search bar, then click on it.
- Click on ‘Virus & Threat Protection’.
- Under Current Threats, click on ‘Scan Options’.
- Check the button next to ‘Custom Scan’ and then click ‘Scan Now’.
- Follow the prompts to select the folders you’d like to scan.
Interpreting Scan Results
After completing any of the above scans, Windows Defender will show you the results. If any malware has been detected, it will be shown under ‘Threats Found’. Clicking on this will provide more details about the detected malware.

Windows Defender will automatically take action on known threats, but may ask for your input for some detected threats. If needed, you can choose actions such as ‘Remove’, ‘Quarantine’, or ‘Allow’ on a per-case basis.
In most cases, ‘Remove’ or ‘Quarantine’ are the safe options. ‘Allow’ should only be used if you are sure the detected software is safe and has been marked as a threat incorrectly.
Furthermore, for ongoing protection, it’s important to ensure Windows Defender’s real-time protection is turned on. This feature will monitor your system continuously for potential threats.
Third-party anti-malware tools
Selection of Reliable Anti-Malware Tools
Select from various legitimate, reliable third-party anti-malware tools available in the market to help protect your Windows system. Tools such as Malwarebytes, Spyhunter, Norton, Combo Cleaner, and Bitdefender are among the most reputable ones, with robust malware detection and removal features. Spend some time researching the right tool for your specific needs and system configuration. Consumer reviews and cybersecurity forums can provide useful insights.
Downloading and Installing Anti-Malware Tools
The next step is downloading and installing your chosen anti-malware tool. Visit the software’s official website to ensure the authenticity of the software and avoid downloading from third-party websites to steer clear of potentially harmful freeware. Follow prompts to install it on your system. Make sure to update it frequently to benefit from the latest malware signatures and detection algorithms.
Performing a Full System Scan
Upon successful installation, it is time to run a scan on your system. This process allows the software to thoroughly check every file and program for potential malware. This might take a while, depending on the size of your system and the specific software you’ve chosen. Be patient, as a full scan provides a comprehensive search that could further protect your system.
Analyzing Scan Results and Initiating Malware Removal
After running the scan, the anti-malware software will generate a report with the infected files and programs. Review this report to understand the threats your system is facing, as some tools can also categorize the malware based on severity.
Once you have an understanding of the threats, follow the software’s recommended steps to remove or quarantine the malware. Some anti-malware applications have an auto-clean feature that fixes the problems automatically. If prompted, restart your system to complete the removal process.
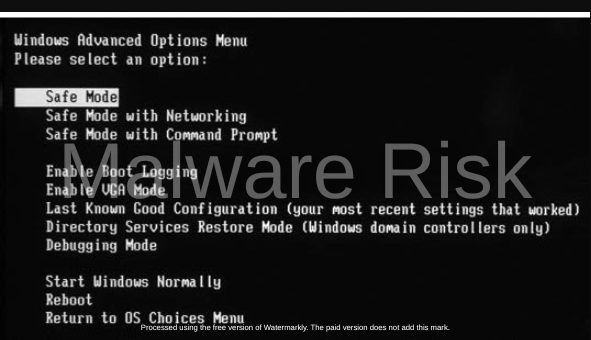
Severe Malware Removal via Safe Mode
If the regular scan wasn’t successful in removing all malware, you might need to boot your system in “Safe Mode”. Safe Mode is a boot option in which the system starts with a minimal set of drivers and services, which can prevent malware from interfering with the removal process. Access Safe Mode by restarting the computer and pressing the F8 key during booting. Once in Safe Mode, run the anti-malware software again to attempt malware removal.
Regular Software Update and Scanning
Following the successful malware removal, keeping your anti-malware software updated is crucial. Updates often include patches for newly discovered malware. Regularly run full system scans – weekly, if possible- to catch and remove potential threats before they can cause significant harm.
Tip: proactive protection and timely detection are key elements in staying ahead of malicious programs and securing your system against malware.
Preventive measures against malware
Recognizing Unsafe Internet Habits
One of the best ways to prevent malware is to exercise safe internet browsing habits. Avoid clicking on suspicious links or downloading files from unverified sources. Phishing emails, often impersonating legitimate companies or contacts, may trick you into clicking a link or downloading a file, which can inject malware into your system. Always verify the sender and the email content before interacting. Be cautious while visiting websites with excessive pop-ups or ones that prompt you to download certain software or tools – they might be malicious.
Implementing Regular Windows Updates
Frequent updates to your operating system (OS) are essential for a healthy computer. Windows often releases updates that fix known vulnerabilities which could be exploited by malware. To ensure your Windows PC is always updated, navigate to the settings and click on ‘Update & Security’. Here, press ‘Check for Updates’ to confirm your system is up-to-date. If not, download and install the necessary updates immediately. Automatic updates can also be activated in this section to avoid manual checking.

Using Firewalls and Real-time Protection
Windows provides built-in firewall and real-time protection features. A firewall acts as the first line of defense against potential threats, stopping any unauthorized access to your computer from the internet. To enable Windows Defender Firewall, go to the ‘Control Panel’, click ‘System and Security’, then select ‘Windows Defender Firewall’. Here, ensure ‘Turn on Windows Defender Firewall’ is activated.

Windows Defender, the built-in anti-malware software on Windows, also has a real-time protection feature. This feature can monitor and block suspicious activities instantly. To enable it, go to ‘Settings’ > ‘Update & Security’ > ‘Windows Security’. Then choose ‘Virus & Threat Protection’ > ‘Manage Settings’. Toggle the ‘Real-time protection’ switch on.
Adopting Additional Preventive Measures
Adding an extra layer of protection can further reduce the risks. Consider using a trusted antivirus or anti-malware software, which can provide real-time scanning and protection against known threats. This software should be updated regularly to keep it effective against the latest threats. Regular backup of data is a preventive measure that can save you from data loss in case malware infection occurs.
Tip: Remember, informed and safe practices can significantly minimize the risk of malware infection. Be vigilant, keep all your software updated, and stay informed about the threats.
Final Thoughts
Mastery over your system’s security necessitates a thorough understanding of the inherent threats and potential defenses. After grasifying the nature of malware and how it operates on Windows systems, empowering yourself to take advantage of Windows Defender becomes an attainable reality. Knowing other anti-malware tools on the market enhances your security arsenal and allows for smart, versatile decisions. Yet, the most potent defense lies in preventing malware from ever reaching your system. Remember, the safest computer habits involve constant vigilance, regular updates, and a reliable firewall. Implementing these measures makes digital hygiene habit-form instead of reactionary, providing you a more secure browsing experience. If you notice something wrong in the steps or article, Click here to suggest

Nishant Verma is a senior web developer who love to share his knowledge about Linux, SysAdmin, and more other web handlers. Currently, he loves to write as content contributor for ServoNode and also collaborated with MRLabs now.