The threat surrounding our online activities remains a pressing concern. Among these, the Aureospoly.co.in browser hijacker has proven to be a significant nuisance. Acting as a virtual bug, it not only alters our online behavior but also introduces unverified websites, unleashing a Pandora’s box of cybersecurity threats.
Quick Links
By assimilating a comprehensive understanding of what this browser hijacker is, one can effectively respond to its pernicious presence. This involves scrutinizing the signs that point towards its existence in your computer, to the manual and automated removal methods to recuperate your virtual integrity.
Understanding Aureospoly.co.in Browser Hijacker
Aureospoly.co.in is recognized as a browser hijacker that seizes control over your web browser settings and manipulates them without your consent. It typically changes your default search engine, homepage, and new tab page to Aureospoly.co.in. The hijacker’s main aim is to drive online traffic to its promoted sites and generate revenue via pay-per-click advertising. While it’s not exactly a virus, its intrusive behavior and potential harm shouldn’t be ignored.

The implications of having Aureospoly.co.in on your browser range from mild annoyance to significant security risks. Besides changing your browser settings, it could also lead to excessive pop-up ads and redirects. It may collect personal data, like your browsing habits and search history, which might be sent to third parties for advertising purposes. You could also be susceptible to phishing attacks, as it may redirect you to unsafe websites that could introduce malware into your system.
Threat Summary:-
| Threat Name: | Aureospoly.co.in |
| Threat Description | It’s a recently discovered browser hijacker or a pop up virus meant to display frequent advert pop ups on screen and encourages users to interact with those. However, the interaction can be disrupting to users in all forms, so it’s better to stay away against those. |
| Threat Type: | Browser Hijacker, Adware, Pop-up Virus |
| Threat Symptoms | Modified settings in browsers, Frequent pop ups or redirect issues while browsing the web, Redirects to fake commercial or suspicious web addresses, etc |
| Threat Distribution | Free Downloads, Deceptive Advertisements, Fake Error Messages, and more. |
| Threat Removal | For efficient detection and removal of this threat, refer to instructions discussed under this guide. |
Infiltration and Associated Threats
Aureospoly.co.in usually infiltrates your system bundled with other free software you download from the internet without your knowledge. This software bundling is a common deceptive technique used by browser hijackers to spread. Also, clicking on phishing emails, harmful ads, or visiting suspicious websites could open the gates for this browser hijacker.

The associated threats with Aureospoly.co.in are concerning. Not only does it change your browser’s settings and expose you to an influx of disruptive pop-up ads, but it also jeopardizes your online security. There is a risk of identity theft and privacy invasion, as it might retrieve information about your browsing activities, personal details, etc. Moreover, if it redirects you to malicious websites, your device could be infiltrated by viruses, ransomware, and other harmful malware.
Understanding Aureospoly.co.in browser hijacker is important before embarking on the removal process. Effective removal entails recognizing the implications, infiltration methods, and associated threats of the hijacker. With this knowledge, you’ll be better equipped to identify and resolve the issue.
Spotting Signs of Aureospoly.co.in browser hijacker
Identifying a Browser Hijack by Aureospoly.co.in
The first step in resolving a browser hijack issue is identifying if your browser has been compromised by Aureospoly.co.in. This involves studying the common symptoms and unwanted alterations this specific hijacker makes to your browser settings. These changes are usually made without your permission and can be quite disruptive to your browsing experience.
Common Symptoms of Aureospoly.co.in Hijack
- One of the most distinct symptoms of Aureospoly.co.in hijack is an unexpected change in the homepage. This means that when you open your browser, you’re instead redirected to the Aureospoly.co.in search engine instead of your preferred homepage.
- In addition, the hijacker is often accompanied by several unwanted pop-up ads that appear frequently while browsing. These intrusive ads can slow down your browser performance and may even redirect you to potentially harmful websites.
- Another red flag is if the default search engine of your browser has been replaced with Aureospoly.co.in. It’s normal to manually change your search engine, but if it changes without your consent, that is a definite sign of a browser hijack.
Unwanted Browser Settings Altered by Aureospoly.co.in
Along with the common symptoms mentioned above, Aureospoly.co.in browser hijacker may also carry out more subtle changes to your browser settings. These alterations may include changing the browser security settings, including disabling the firewall and antivirus protections without your knowledge.
Additionally, you might notice the addition of new, unwanted browser extensions or toolbars. This contributes to the slow performance of your browser and could also lead to reduced browser security.
Finally, Aureospoly.co.in browser hijacker might also modify your browser’s shortcut settings. This is done by altering the Target field of the browser’s shortcut on your desktop or taskbar, which would cause the browser to open Aureospoly.co.in every time it is launched.
Identifying these signs and unwanted alterations to your browser settings is crucial. Confirmation of these changes confirms the presence of a browser hijacker, which guides your next steps for removal of the Aureospoly.co.in.
Remove Aureospoly.co.in Hijacker Manually
Before you start deleting or removing files, it’s important to first ensure that your computer is indeed infected with the Aureospoly.co.in browser hijacker. You might notice your computer behaving erratically, your browser redirects you to different websites, or you may see unexpected pop ups. This is a strong indication the hijacker is present on your computer.
Uninstalling Suspicious Programs
Open the control panel or system settings on your computer. Look for ‘Add or Remove Programs’ in Windows, or ‘Applications’ if you’re using a MacOS. Search through the list of installed programs and uninstall any applications that look suspicious or you don’t remember installing. It’s recommended you sort the programs by date and remove those which were installed during the period symptoms of the browser hijacker started appearing.


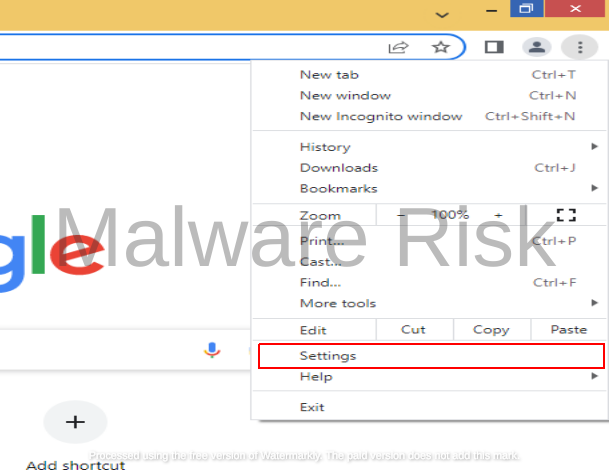
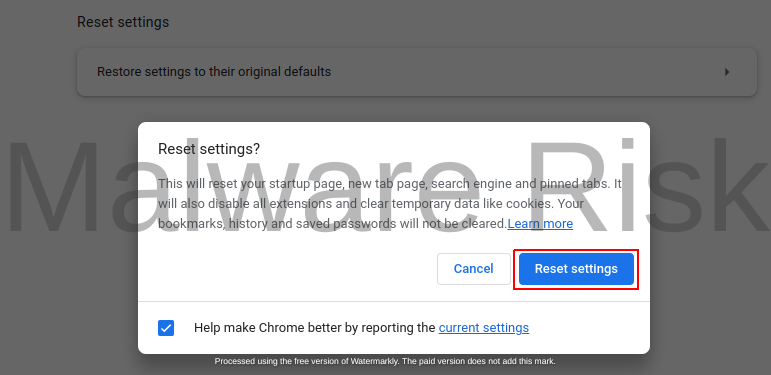
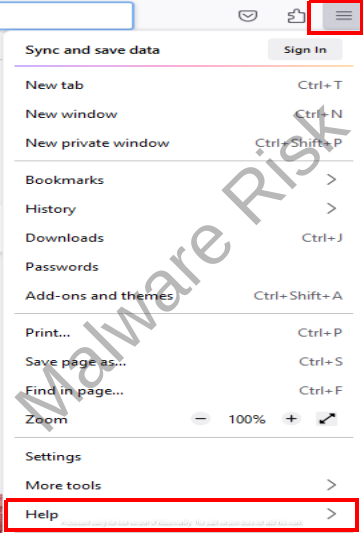
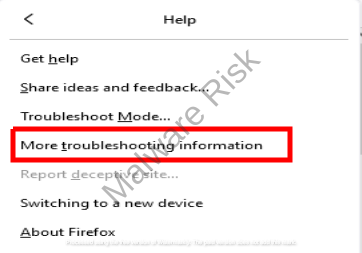
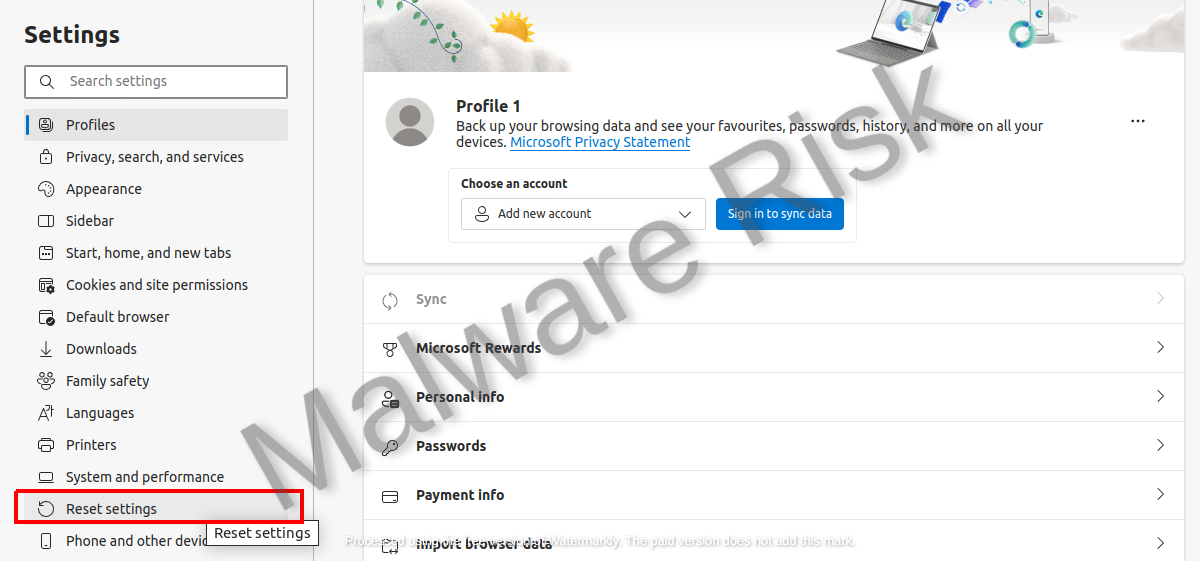
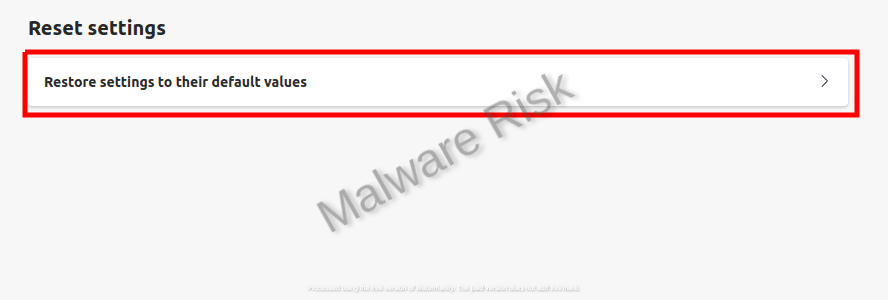
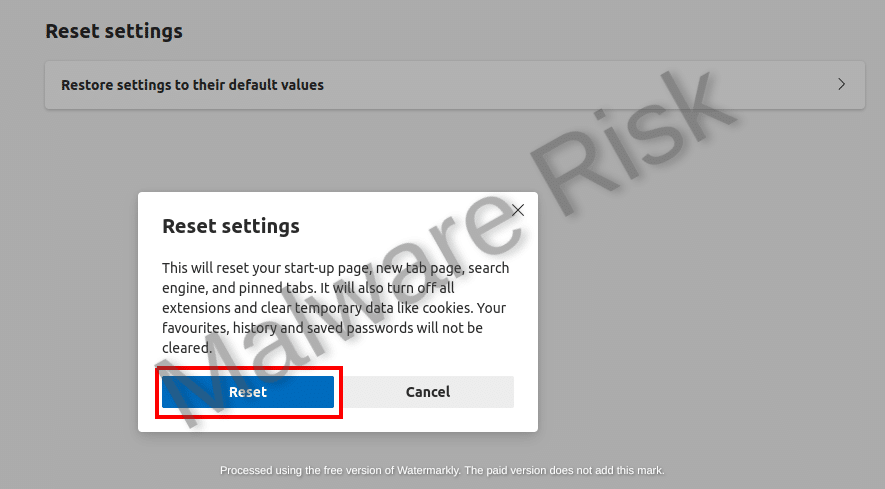
Resetting your Web Browser Settings
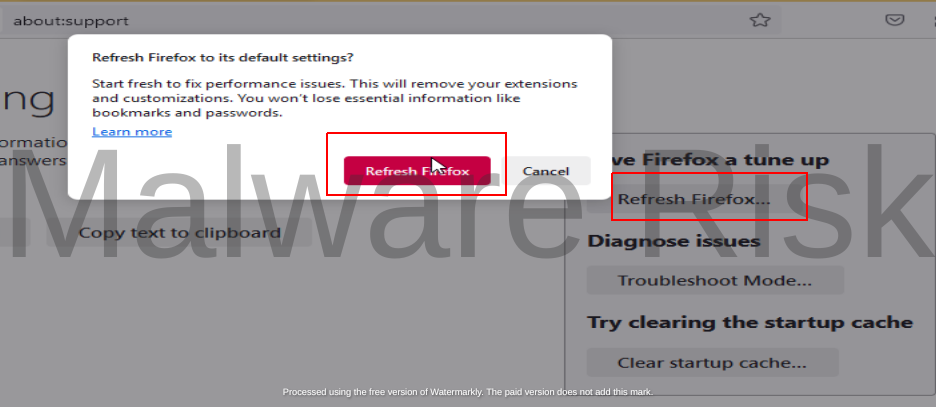
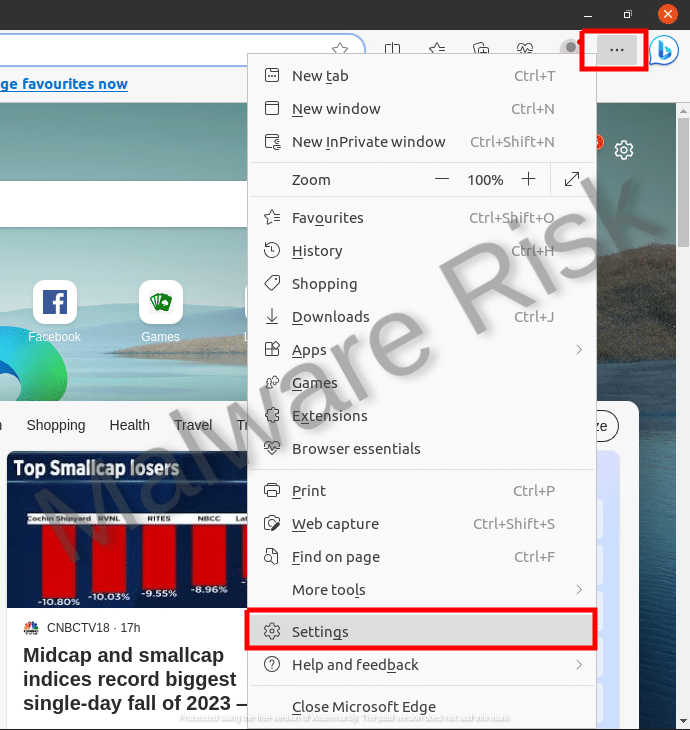
In circumstances where the browser hijacker has altered your web browser settings, resetting your settings can resolve the problem. Get through the instructions based on browser variants respectively:
Step 1: Launch Google Chrome on your Windows computer.
Step 1: Launch Firefox on your Windows.
Step 1: Launch Edge and click on the three horizontal lines in top-right corner.
Resetting Safari on a Mac involves diverse steps like clearing the browsing history, emptying the cache, and removing extensions and cookies. Clearing Browsing History in Safari To clear your browsing history in Safari, click on "History" in the top menu, then select "Clear History." A dropdown menu will appear where you can select the length of history you want to clear - "the last hour," "today," "today and yesterday," or "all history." Choose the option that suits your requirement and click "Clear History."
Emptying Safari’s Cache The cache is a place where Safari stores website data to speed up the loading process. Over time, the cache can become bloated and may slow down Safari. To clear it, click on the "Safari" in the top menu, then select "Preferences." From there, go to the "Advanced" tab and select "Show Develop menu in menu bar." Close the "Preferences" window, and in the top menu, you'll find a new "Develop" option. Clicking on it will give you the option to "Empty Caches."
Removing Cookies in Safari Removing cookies can be done through the "Preferences" menu in Safari. Click on "Safari" then "Preferences," then go to the "Privacy" tab. You can either "Manage Website Data" to remove cookies from specific sites, or click "Remove All Website Data" to remove all cookies.
Removing Extensions in Safari Extensions are small software programs that can modify and enhance the functionality of the Safari browser. But sometimes, they might cause issues. To remove them, click on "Safari" in the top menu, then "Preferences". Go to the "Extensions" tab, where you'll see the list of installed extensions. Select the extensions you want to remove and click on the "Uninstall" button.
Access Internet Explorer SettingsClick on Internet Explorer to open the application on your computer. After opening Internet Explorer, locate the "Tools" icon. This icon typically looks like a small gear in the upper-right corner of the Internet Explorer window. Once you've clicked on this, a dropdown menu will appear. From this menu, select "Internet Options."
Understand the Implications of ResettingBefore resetting, understand what it means to reset Internet Explorer to factory defaults. By doing so, you're erasing any personal settings, extensions, or cookies you've set up since you've installed the software. This includes deleting your browsing history, disabling toolbars and add-ons, and resetting all custom settings to default. If you have any important bookmarks or saved passwords, make sure to back them up first. Navigate to the Reset OptionIn the "Internet Options" window, click on the "Advanced" tab. At the bottom of this tab, you should see a "Reset..." button. Click on this to open up the "Reset Internet Explorer Settings" window.
Execute the ResetAfter the "Reset Internet Explorer Settings" window opens, you'll see a box that you can check to "Delete personal settings." If you want to erase all personal data saved in Internet Explorer, including saved passwords, form data, and browsing history, check this box. If you'd rather keep your personal data and only reset the browser settings to default, leave this box unchecked. Once you've decided what you want to do, click the "Reset" button at the bottom. A confirmation window will appear to assure you that the reset was successful.
Verify the Successful ResetAfter you click "Reset", Internet Explorer will apply the changes and ask you to restart the software. Close Internet Explorer and open it again. The changes have now taken effect and your software has been reset to factory settings. To confirm the reset, navigate back to the "Tools" menu, select "Internet Options", and click on the "Advanced" tab. At the bottom of this window, you should see that your personal settings have either been erased or reset, depending on your previous selection. If executed correctly, Internet Explorer should now operate just as it did when you originally installed it. Resetting Opera on Windows
Resetting Opera on Mac
|
Checking your Computer’s Shortcuts
Hijackers often modify your shortcuts to ensure that you’re redirected to their page every time you open your browser. To correct this, right click on your browser’s shortcut and select ‘Properties’. Look for a field called ‘Target’. Ensure that this field only contains the location of the program and nothing else.

Protecting Your Computer in the Future
After successfully removing Aureospoly.co.in, it’s critical to take steps to prevent such issues in the future. Update your operating system and browser regularly. In addition, ensure that you download software from reliable sources and be vigilant about the permissions you grant to applications. Regularly scanning your computer with an anti-malware tool can help catch such threats before they cause problems.
Antivirus software to remove Aureospoly.co.in
Identifying The Threat: Aureospoly.co.in
Aureospoly.co.in browser hijacker is a malicious software that changes your browser settings, redirects your search results to unwanted websites, and may even anticipate your search queries or record your online activities. This malware can be challenging but not impossible to remove.
The Right Antivirus or Malware Removal Tool
There are many antivirus or malware removal tools available in the market. Some of them include Norton, Spyhunter, Combo Cleaner, and Malwarebytes. Each of these software has its unique features but all are effective in detecting and removing threats like Aureospoly.co.in.
When choosing the right tool, consider the software’s compatibility with your operating system, ease of use, effectiveness in detecting and removing threats, and customer reviews and test reports.
Using the Antivirus or Malware Removal Tool
Threat Removal With Malwarebytes Malwarebytes is a leading provider of antimalware software, dedicated to protecting users from the ever-growing threat of malware. With its advanced technology and comprehensive approach, Malwarebytes offers a robust solution to detect, prevent, and remove malicious software from computers and devices. Malwarebytes' antimalware software combines multiple layers of protection, including real-time scanning, behavior monitoring, and artificial intelligence, to identify and eliminate threats in real-time. This proactive approach ensures that users are protected from both known and emerging threats. It’s available as a free tool and we recommend it as a must have app on your device to keep your protected against threats. Step 1: Download Malwarebytes for your device by clicking on the link based on your operating system. Malwarebytes is available free of cost and can be used over cross platforms. However, the premium version offers more versatile features and protection to your device. You can register the app to premium version through in-app options or official website. Download Malwarebytes For Windows/Mac Step 2: Navigate to the folder where the installer file is downloaded and double click on it. The file is usually stored under “Downloads” directory.
Step 3: Once the installer runs, it opens Malwarebytes Setup Wizard with two options as Install and Advanced options. The Advanced option basically allows you to choose a directory where you want the app to install, select your language, and adding shortcuts. Just click on Install.
Step 4: You will now be asked to choose the type of protection you want, either Personal or Business. Based on your requirements, select the right option and click Next button.
Step 5: The setup will ask you to add a browser guard to keep your browsing safe. It’s an optional thing, but still you can choose adding the plugin to browsers to keep your online data safe. Once selected the appropriate option, proceed further to install the app. The installation process may end in a few minutes.
Step 6: After the installation is successfully done you can see a success notice. Click on Open Malwarebytes button now.
Step 7: After the Malwarebytes launches, click on the Scan button to start the scanner to identify present threats on your device.
Step 8: Sit back, wait and relax till the scanner searches for malicious traits on your computer. It may take time depending upon the storage size, and computer resources as well.
Step 9: After the scanning process completes, a screen with detected threats will appear before you. To remove detected malware or potentially unwanted programs from your device, click on Quarantine button.
Step 10: Malwarebytes may also ask you to restart your computer to complete threat removal process. So, just restart your computer. That’s it, your computer is now malware free. Threat Removal With Spyhunter SpyHunter is a powerful antimalware software designed to protect your computer from various threats, including malware, spyware, and adware. With its advanced scanning technology, SpyHunter can detect and remove harmful programs that may be lurking in your system. It also offers real-time protection to prevent new infections from occurring. SpyHunter is known for its user-friendly interface, making it easy for both novice and experienced users to navigate. It provides regular updates to ensure that your computer remains secure against the latest threats. If you're looking for a reliable antimalware solution, SpyHunter is definitely worth considering. Step 1: Download Spyhunter 5 for your device by clicking on the link based on your operating system. SpyHunter 5 Anti-Malware provides a 7-day fully functional Free Trial (15 days for Mac) with Credit card required, No charge will apply upfront. No charge if you cancel 2 business days before the trial ends. Download Spyhunter For Windows Download Spyhunter For Mac Step 2: Go to the directory where the installer is downloaded and stored. The file is usually stored under “Downloads” directory. Double click on the installer to run setup.
Step 3: Select your preferred language and click on OK button. This will initialize the installer, so click on the Continue button when prompted.
Step 4: You will be asked to accept the EULA and Privacy policy of the application to proceed the installation. So choose the option I accept the EULA and Privacy Policy, and click on Accept & Install Button.
Step 5: Now, the installation process will begin and progress bar can be seen. The process may take a while to complete, after which a successful installation notice is shown.
Step 6: The Spyhunter launches itself automatically following installation. Below mentioned screen will appear before you.
Step 7: Also, the scanner will start scanning your computer to identify present threats inside your device. During scan, it will show you detected threat’s name, security level, and details about the threat as well. Sit back & relax to complete the scan process
Step 8: The scanner once finished, click on Next button to proceed further.
Step 9: The app will ask you to buy its licensed version to complete the removal process. Alternatively, you can also avail a 7 day free trial under which the software will be fully functional to remove all threats.
Threat Removal With Combo Cleaner Combo Cleaner is a comprehensive security software designed to protect and optimize your Mac system. With its powerful features and user-friendly interface, Combo Cleaner offers a range of tools to keep your device safe from malware, adware, viruses, and other threats. It scans your computer thoroughly, detects and removes any malicious software it finds, and also cleans up junk files and unnecessary clutter to improve system performance. Combo Cleaner is known for its advanced algorithms and real-time protection, ensuring that your Mac remains secure and optimized at all times. Whether you are a casual user or a professional, Combo Cleaner provides a reliable solution to ensure the safety and efficiency of your Mac. Step 1: Click download button below to get Combo Cleaner for Windows/Mac on your device. Combo Cleaner Antivirus is available to download as free scanner. The scanner will scan and detect all inside threats on device, but users need to buy its license key to avail complete removal of threats. Download ComboCleaner For Windows Download ComboCleaner For Mac Step 2: Browse to the directory where the installer is downloaded (usually in ‘Downloads’ folder), and double click on the installer to start installation.
Step 3: The installer begins and will ask you to set some necessary parameters like creating shortcuts, starting the app on windows startup and more. Choose the right options based on your needs, and click Next button.
Step 4: The installer now starts to install Combo Cleaner on your device and will complete it in just a few minutes.
Step 5: Once the installation completes, click on Finish button. Do make sure the option “Launch Combo Cleaner and run initial computer scan” is checked.
Step 6: The initial computer scan will start with updating and installing Combo Cleaner antimalware database updates. It will take some time depending upon your internet speed, and other resources.
Step 7: After the database updates are successfully installed, the antimalware solution will start scanning your device for present malware threats. Sit back and relax to let the app complete its process.
Step 8: After the scanning completes, a screen appears with all detected threats on your device. Just click on Remove All Threats button. Threat Removal With Norton Antivirus Norton 360 is a comprehensive antivirus software that offers robust protection against various online threats. With its advanced features and real-time scanning capabilities, it ensures the safety of your devices and personal information. This antivirus software not only detects and removes viruses, malware, and spyware but also provides a firewall to protect your network from unauthorized access. Norton 360 is compatible with multiple platforms, including Windows, Mac, and mobile devices, providing a seamless experience across all your devices. Its user-friendly interface allows you to easily navigate through its various features and customize your security settings according to your preferences. Stay protected with Norton 360 and enjoy a worry-free online experience. Step 1: Click on the button below to get Norton 360 protection for your device. Norton 360 Antivirus is available and accessible over cross platforms. It provides a 7 day fully functional free trial with Credit Card. No charge deduction till trial period. Download Norton 360 For Windows/Mac Step 2: Download the installer and run it on your device. Click on Install button to proceed with installation steps further.
Step 3: The installation process will begin now with an increasing progress bar. Wait for the installation to complete.
Step 4: After the installation process completes, launch Norton 360 and click on Quick Scan option to start scanning device for threats.
Step 5: The scanner will initialize scanning computer for threats. This process may take some time depending upon the disk size and hardware resources of device.
Step 6: Once the scanner finishes, it will take all appropriate action against detected threats automatically. Click on Finish button to close the app.
Step 7: If you have purchased Norton’s license key, we suggest you to activate the application by clicking on Activate Now option.
Step 8: Norton 360 will now connect with its server to complete activation.
Step 9: Congratulations, your device is now protected with Norton 360 against all threats. |
Effective Use of Antivirus or Malware Removal Tool
Regularly perform full scans on your device – ideally once a week. Regular updates of antivirus software are critical to ensure that all newly emerging threats can be detected.
Antivirus or malware removal tools can also offer real-time protection, scanning downloaded files and programs for threats before they’re opened or installed. Enable this feature if available.
Tip To Remember: No antivirus or malware removal tool is 100% effective, therefore practicing safe browsing habits such as not clicking on suspicious links or downloading files from untrusted sources will enhance your system’s protection against threats like Aureospoly.co.in.
Wrapping Up
Mastering the art of protecting and safeguarding one’s digital footprint in the current risk-prone cyberspace landscape is imperative. Yielding a deeper comprehension of Aureospoly.co.in browser hijacker, spotting its offensive signs, eradicating it manually, and employing antivirus software for removal, are all, undoubtedly, essential steps towards ensuring one’s cyber wellness. Adopting these strategies and applying them effectively can indeed help us navigate through any under-the-radar virtual threat, thereby ensuring the sanctity of our online experience remains uncompromised.
Frequently Asked Questions about Virus/Malware
A computer virus is a type of malware that spreads between computers and damages data and software. It is a program that infects files or system areas and makes copies of itself. Some viruses are harmless, while others can damage or destroy files. Unlike worms, viruses require user action to spread. They used to be spread through portable media, but now they are primarily spread through email messages. To avoid virus infections, it is important to not open unknown email attachments and to view email messages in plain text.
Viruses spread by infecting files or the system areas of a computer's hard drive and making copies of themselves. They can infect other programs on the same computer or on other computers connected over a network. In the past, viruses were primarily spread through portable media such as floppy disks, but now they are mainly spread through email messages. When you open an attachment or click a link in an email message, most viruses are activated. It is important to be cautious of email attachments and links, limit HTML in email messages, and view them in plain text to avoid virus infections.
A worm is a type of malware or malicious software that can rapidly replicate and spread across devices within a network. Unlike a virus, a worm can self-replicate and spread automatically without the need for human intervention. Worms can infect computers through software vulnerabilities, spam email or instant message attachments, or removable drives. Once a worm infects a device, it continues to spread to other systems, causing disruptions and potential data loss. Mitigating a worm attack involves containment, inoculation, quarantine, and treatment. It is crucial for businesses to have a coordinated response plan in place to effectively respond to worm attacks.
A Trojan Horse, or Trojan, is a type of malware that disguises itself as legitimate software or code. Unlike viruses or worms, Trojans require deliberate action from the user to infect a device. Once installed, Trojans can perform various actions, such as modifying data, stealing sensitive information, exploiting vulnerabilities, installing malicious programs, extorting users, setting up backdoor access, or carrying out DDoS attacks. There are different types of Trojans, including exploit Trojans, downloader Trojans, ransom Trojans, backdoor Trojans, fake AV Trojans, rootkit Trojans, SMS Trojans, banking Trojans, and Trojan GameThief. Some recent examples of Trojan attacks include Zloader, QakBot, and Andromeda.
Adware and browser hijackers are similar in some ways but have distinct differences. Adware is a type of software that displays unwanted advertisements on a user's device. It is often bundled with freeware or shareware and can track user behavior and collect personal information. On the other hand, browser hijackers are a specific type of malware that modifies browser settings without the user's consent, redirecting them to malicious websites. While adware may be a component of browser hijackers, not all adware is classified as browser hijackers. Both adware and browser hijackers can negatively impact user experience and compromise privacy and security. It is essential to have proper security measures in place to protect against both adware and browser hijackers.
Ransomware is a type of malware that encrypts a victim's data and holds it hostage until a ransom is paid. It prevents users from accessing their systems or files by either locking the screen or encrypting the files themselves. Ransomware can spread across networks and paralyze entire organizations. It uses asymmetric encryption, which makes it extremely difficult to decrypt files without the private key. Ransomware is often distributed through email spam campaigns or targeted attacks. It has been on the rise since the WannaCry outbreak in 2017 and has become more sophisticated, incorporating techniques like data theft and double extortion to pressure victims into paying the ransom.
To protect your computer from viruses, you can follow these steps:
- Install antivirus software: Use reputable antivirus software and keep it updated to detect and remove viruses.
- Keep software up to date: Regularly update your operating system and software to patch any security vulnerabilities.
- Backup your computer: Regularly backup your important files to an external storage device or cloud storage to protect against data loss from viruses.
- Use strong passwords: Create strong, unique passwords for your accounts to prevent unauthorized access.
- Be cautious of downloads: Avoid downloading files from untrusted sources and be cautious of email attachments, as they can contain viruses.
- Install an ad-blocker: Ad-blocking software can help prevent malicious ads that may contain viruses.
- Run virus scans regularly: Schedule regular virus scans on your computer to detect and remove any malware.
- Avoid suspicious links: Be cautious when clicking on links, especially in email messages, as they can lead to malicious websites. Hover over links to verify their legitimacy before clicking.
By following these steps and exercising caution while browsing, you can minimize the risk of viruses infecting your computer.
The signs of a malware infection include slow performance, unexpected freezing or crashing, diminished storage space, changes to your browser homepage, browser redirects, new browser toolbars, annoying pop-ups, unusual error messages, fake virus alerts, excessive ads, system crashes, loss of disk space, increased internet activity, changes in browser settings, disabled antivirus software, and loss of access to files. These symptoms indicate that your device may be infected with malware and should be diagnosed and treated promptly.
To avoid falling for tech support scams related to malware, you can follow these tips:
- Be cautious of unsolicited phone calls claiming to be tech support. Legitimate companies usually don't reach out to customers in this manner.
- Never call the phone number in a pop-up message on your computer. These pop-ups can be fake and are often used as a tactic by scammers.
- Update or download legitimate security software and regularly scan your computer for malware. Delete anything the software identifies as a problem. If you need assistance, seek help from trusted sources.
- Be skeptical of anyone claiming to be a tech support staffer from a reputable company like Microsoft. Don't provide personal information or grant remote access to your computer unless you've verified their identity.
- Educate yourself about common scam techniques and stay informed about the latest threats. This will help you recognize red flags and avoid falling for scams.
If your device is infected with malware, there are several steps you can take to address the issue:
- Confirm the infection: Look for unusual behavior on your device, such as slow performance, frequent crashes, or excessive pop-up ads. This will help you determine if your device is indeed infected with malware.
- Disconnect from the internet: Unplug your device from the network to prevent the malware from spreading or communicating with its command and control servers.
- Run anti-malware software: Use reputable anti-malware software to scan your device and remove the malware. Make sure the software is up to date and perform a thorough scan of your system.
- Back up critical files: Before taking any further action, back up your important files and data to ensure they are not lost during the malware removal process.
- Reinstall the operating system if necessary: If the malware has deeply infected your device and cannot be completely removed, consider reinstalling the operating system. This will wipe out all the existing data and software on your device, so make sure you have backups of your important files.
- Consider data recovery services: If you have lost any data due to the malware infection or the subsequent removal process, you may want to consult professional data recovery services to retrieve your lost files.
Remember to keep your device's software up to date, use strong passwords, and be cautious of suspicious links and downloads to prevent future malware infections.

Nishant Verma is a senior web developer who love to share his knowledge about Linux, SysAdmin, and more other web handlers. Currently, he loves to write as content contributor for ServoNode and also collaborated with MRLabs now.