As part of this cyber era, understanding the various facets of ITQW Ransomware becomes a key aspect in the broader sphere of cybersecurity. Known for paralyzing systems, encrypting files and demanding ransom in return for the decryption key, ITQW Ransomware has created a niche for itself in the cybercrime underworld. We venture into a comprehensive understanding of ITQW Ransomware, its modus operandi, and the methods through which it can infiltrate your system.
Quick Links
On our journey, we shed light on recognizing the signs of a ransomware attack and the crucial process of tracing and isolating such infections. Ensuring the best use of anti-malware tools and configuring system settings are other areas we touch upon to provide a 360-degree view of handling ITQW Ransomware.
Intro To ITQW Ransomware
Ransomware has become a foreboding word in the tech sphere, synonymous with fear, frustration, and potential financial loss. One player in this cybercriminal field that’s currently making waves is ITQW Ransomware. Designed with stealth and destruction in mind, getting to grips with what ITQW Ransomware really is, and how it infects its victims, is paramount.

Ransomware, in its simplest form, is malicious software programmed to encrypt a computer user’s files and demand a ransom for their decryption. ITQW Ransomware is a variant in this genus of cyber threats, belonging to the expansive Stop (Djvu) Ransomware family. It targets Windows PCs primarily and leaves its mark by appending “.itqw” to all affected files.
Infiltration Explained
Unlike certain less sophisticated strains of ransomware, ITQW does not merely hitch a free ride with other software installations or piggyback on spam emails. This stealthy saboteur utilizes much craftier infiltration methods.
- Torrents and illegal activation tools often harbor ITQW Ransomware preying on the fringes of the digital underground. Figures show a correlation between computers infected with ITQW Ransomware and the use of pirated software or software cracks, underlining the risk associated with these unregulated corners of the web.
- Software vulnerabilities also present an open window for ITQW Ransomware. Often exploiting outdated or under-protected systems, this ransomware does not hesitate to infiltrate through the digital cracks. Regular software updates, therefore, become not just an advantage, but a necessity in preventing its spread.
- But the infection methods do not end there. Scam websites promising too-good-to-be-true offers or displaying intrusive pop-up ads are also frequented by ITQW Ransomware. Subsequently, users who wade through these untrustworthy digital lanes risk inviting this unwelcome guest into their computer.
Measures To Consider Post Removal
While dealing with ITQW Ransomware post-infection is an arduous and often costly pursuit, a strong suite of preventive measures might very well keep this menace at bay. Perfecting the art of digital scepticism – avoiding untrusted downloads, maintaining software updates, and steering clear of sketchy websites – could spell the difference between sailing the digital world unscathed or falling prey to this cyber saboteur.

As ransomwares continue to evolve and adapt, staying ahead of the curve requires constant vigilance. Understanding the mechanics behind the likes of ITQW Ransomware, and considering the potential vulnerability of your digital workspace, is the prudent tech enthusiast’s first line of defense. After all, in an arena where knowledge truly is power, information might be the greatest antivirus available.
Detecting ITQW Ransomware on Your System
Accurate detection of ITQW ransomware on your system is the first line of defense. While most instances involve a notification popping up on your screen with ransom demands, subtle signs can also alert you to its presence. Look for unexpected changes in file names, mainly those with an awkward ITQW extension, and sluggish computer performance. This ransomware significantly impacts CPU usage as it encrypts files, taking up considerable system resources.
Your next line of defense is your antivirus program, which should ideally be equipped to detect such threats, including ITQW ransomware. Ensure it’s updated with the latest virus definitions. Antivirus software uses techniques such as signature-based detection, heuristic analysis, sandboxing, and data mining to identify ransomware.
Isolating ITQW Ransomware
Once identified, isolating ITQW ransomware from the rest of the system is crucial to mitigate the damage. For this, you will need to place your system in Safe Mode. In this diagnostic mode, your system runs with a minimum set of drivers and services. ITQW ransomware, like most malware, thrives when all system functions and internet connections are active. By limiting these, Safe Mode effectively isolates the ransomware, which can then be more easily removed.
To enable Safe Mode on a Windows system, restart your computer and press the F8 key during startup. From the displayed menu, select the ‘Safe Mode with Networking’ option. Mac users can achieve a similar state by booting into Recovery Mode.
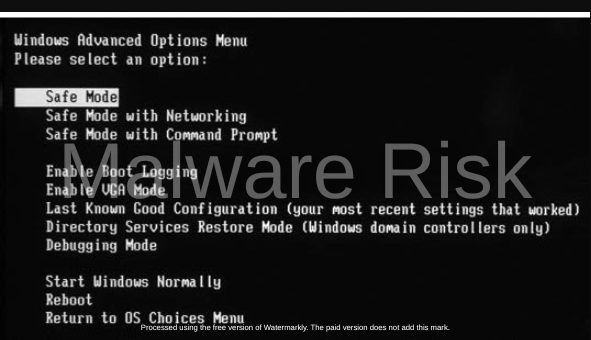
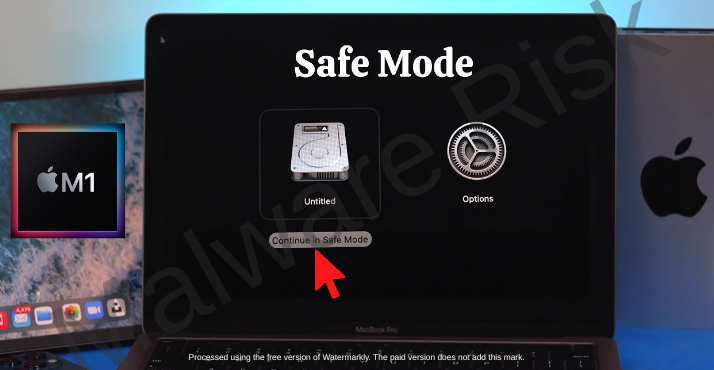
Another way to isolate the ransomware is to disconnect your computer from any network. This could help prevent ITQW from spreading to other devices connected to the same network.

Keep in mind that detection and isolation are often not enough to fully eliminate ransomware from your system, but they provide a head start in the eradication process. ITQW ransomware can persist through its hidden components, left dormant on your system. Reliable antivirus software or professional IT assistance may be required to ensure thorough and safe removal.
In the world of cybersecurity, being aware of the threats and staying one step ahead is vital. Detection and isolation of threats like ITQW ransomware are vital skills amidst the ever-evolving scenarios of cyber threats.
ITQW Ransomware Removal Guide
Let’s continue our discussion with reliable methods for ITQW Ransomware removal. Once your system has been identified as infected, and the malware isolated, pinpoint and systematic deletion remains crucial. Use reputable, security-focused utilities like Spyhunter, Malwarebytes, Combo Cleaner, etc to eradicate this menace. These tools meticulously scan every file on your system, ensuring a comprehensive cleanse from ITQW Ransomware.
Threat Removal With Malwarebytes Malwarebytes is a leading provider of antimalware software, dedicated to protecting users from the ever-growing threat of malware. With its advanced technology and comprehensive approach, Malwarebytes offers a robust solution to detect, prevent, and remove malicious software from computers and devices. Malwarebytes' antimalware software combines multiple layers of protection, including real-time scanning, behavior monitoring, and artificial intelligence, to identify and eliminate threats in real-time. This proactive approach ensures that users are protected from both known and emerging threats. It’s available as a free tool and we recommend it as a must have app on your device to keep your protected against threats. Step 1: Download Malwarebytes for your device by clicking on the link based on your operating system. Malwarebytes is available free of cost and can be used over cross platforms. However, the premium version offers more versatile features and protection to your device. You can register the app to premium version through in-app options or official website. Download Malwarebytes For Windows/Mac Step 2: Navigate to the folder where the installer file is downloaded and double click on it. The file is usually stored under “Downloads” directory.
Step 3: Once the installer runs, it opens Malwarebytes Setup Wizard with two options as Install and Advanced options. The Advanced option basically allows you to choose a directory where you want the app to install, select your language, and adding shortcuts. Just click on Install.
Step 4: You will now be asked to choose the type of protection you want, either Personal or Business. Based on your requirements, select the right option and click Next button.
Step 5: The setup will ask you to add a browser guard to keep your browsing safe. It’s an optional thing, but still you can choose adding the plugin to browsers to keep your online data safe. Once selected the appropriate option, proceed further to install the app. The installation process may end in a few minutes.
Step 6: After the installation is successfully done you can see a success notice. Click on Open Malwarebytes button now.
Step 7: After the Malwarebytes launches, click on the Scan button to start the scanner to identify present threats on your device.
Step 8: Sit back, wait and relax till the scanner searches for malicious traits on your computer. It may take time depending upon the storage size, and computer resources as well.
Step 9: After the scanning process completes, a screen with detected threats will appear before you. To remove detected malware or potentially unwanted programs from your device, click on Quarantine button.
Step 10: Malwarebytes may also ask you to restart your computer to complete threat removal process. So, just restart your computer. That’s it, your computer is now malware free. Threat Removal With Spyhunter SpyHunter is a powerful antimalware software designed to protect your computer from various threats, including malware, spyware, and adware. With its advanced scanning technology, SpyHunter can detect and remove harmful programs that may be lurking in your system. It also offers real-time protection to prevent new infections from occurring. SpyHunter is known for its user-friendly interface, making it easy for both novice and experienced users to navigate. It provides regular updates to ensure that your computer remains secure against the latest threats. If you're looking for a reliable antimalware solution, SpyHunter is definitely worth considering. Step 1: Download Spyhunter 5 for your device by clicking on the link based on your operating system. SpyHunter 5 Anti-Malware provides a 7-day fully functional Free Trial (15 days for Mac) with Credit card required, No charge will apply upfront. No charge if you cancel 2 business days before the trial ends. Download Spyhunter For Windows Download Spyhunter For Mac Step 2: Go to the directory where the installer is downloaded and stored. The file is usually stored under “Downloads” directory. Double click on the installer to run setup.
Step 3: Select your preferred language and click on OK button. This will initialize the installer, so click on the Continue button when prompted.
Step 4: You will be asked to accept the EULA and Privacy policy of the application to proceed the installation. So choose the option I accept the EULA and Privacy Policy, and click on Accept & Install Button.
Step 5: Now, the installation process will begin and progress bar can be seen. The process may take a while to complete, after which a successful installation notice is shown.
Step 6: The Spyhunter launches itself automatically following installation. Below mentioned screen will appear before you.
Step 7: Also, the scanner will start scanning your computer to identify present threats inside your device. During scan, it will show you detected threat’s name, security level, and details about the threat as well. Sit back & relax to complete the scan process
Step 8: The scanner once finished, click on Next button to proceed further.
Step 9: The app will ask you to buy its licensed version to complete the removal process. Alternatively, you can also avail a 7 day free trial under which the software will be fully functional to remove all threats.
Threat Removal With Combo Cleaner Combo Cleaner is a comprehensive security software designed to protect and optimize your Mac system. With its powerful features and user-friendly interface, Combo Cleaner offers a range of tools to keep your device safe from malware, adware, viruses, and other threats. It scans your computer thoroughly, detects and removes any malicious software it finds, and also cleans up junk files and unnecessary clutter to improve system performance. Combo Cleaner is known for its advanced algorithms and real-time protection, ensuring that your Mac remains secure and optimized at all times. Whether you are a casual user or a professional, Combo Cleaner provides a reliable solution to ensure the safety and efficiency of your Mac. Step 1: Click download button below to get Combo Cleaner for Windows/Mac on your device. Combo Cleaner Antivirus is available to download as free scanner. The scanner will scan and detect all inside threats on device, but users need to buy its license key to avail complete removal of threats. Download ComboCleaner For Windows Download ComboCleaner For Mac Step 2: Browse to the directory where the installer is downloaded (usually in ‘Downloads’ folder), and double click on the installer to start installation.
Step 3: The installer begins and will ask you to set some necessary parameters like creating shortcuts, starting the app on windows startup and more. Choose the right options based on your needs, and click Next button.
Step 4: The installer now starts to install Combo Cleaner on your device and will complete it in just a few minutes.
Step 5: Once the installation completes, click on Finish button. Do make sure the option “Launch Combo Cleaner and run initial computer scan” is checked.
Step 6: The initial computer scan will start with updating and installing Combo Cleaner antimalware database updates. It will take some time depending upon your internet speed, and other resources.
Step 7: After the database updates are successfully installed, the antimalware solution will start scanning your device for present malware threats. Sit back and relax to let the app complete its process.
Step 8: After the scanning completes, a screen appears with all detected threats on your device. Just click on Remove All Threats button. Threat Removal With Norton Antivirus Norton 360 is a comprehensive antivirus software that offers robust protection against various online threats. With its advanced features and real-time scanning capabilities, it ensures the safety of your devices and personal information. This antivirus software not only detects and removes viruses, malware, and spyware but also provides a firewall to protect your network from unauthorized access. Norton 360 is compatible with multiple platforms, including Windows, Mac, and mobile devices, providing a seamless experience across all your devices. Its user-friendly interface allows you to easily navigate through its various features and customize your security settings according to your preferences. Stay protected with Norton 360 and enjoy a worry-free online experience. Step 1: Click on the button below to get Norton 360 protection for your device. Norton 360 Antivirus is available and accessible over cross platforms. It provides a 7 day fully functional free trial with Credit Card. No charge deduction till trial period. Download Norton 360 For Windows/Mac Step 2: Download the installer and run it on your device. Click on Install button to proceed with installation steps further.
Step 3: The installation process will begin now with an increasing progress bar. Wait for the installation to complete.
Step 4: After the installation process completes, launch Norton 360 and click on Quick Scan option to start scanning device for threats.
Step 5: The scanner will initialize scanning computer for threats. This process may take some time depending upon the disk size and hardware resources of device.
Step 6: Once the scanner finishes, it will take all appropriate action against detected threats automatically. Click on Finish button to close the app.
Step 7: If you have purchased Norton’s license key, we suggest you to activate the application by clicking on Activate Now option.
Step 8: Norton 360 will now connect with its server to complete activation.
Step 9: Congratulations, your device is now protected with Norton 360 against all threats. |
Keep your system in Safe Mode throughout the operation to minimize the ransomware’s field of action. This could be done by restarting your device and pressing the F8 key during the startup process. From the displayed options, select ‘Safe Mode with Networking’ to proceed with malware removal tools and not risk a fresh infection as you eradicate the present one.
Profound removal methodologies aren’t always successful and may warrant elevated efforts to eliminate ITQW Ransomware. System Restore can work significantly here. Tap into your system’s memory and set it back to a checkpoint created before the ITQW Ransomware infection. Remember, for this method to work, the System Restore function must have been enabled prior to the attack.
Recovery Of Data Post Removal
Once you’ve expunged ITQW Ransomware from your device, attention must shift to restitution. This cyclopean task often begs the question: “How to recover the system post-removal?” Here, a sound backup strategy proves crucial. Complete system backups, done frequently on an external hard drive or a cloud service, ensure disaster recovery becomes a smoother process.
Sadly, not everyone has the habit of backing-up routinely. If you fall into this category, despair not for all isn’t lost. Shadow Explorer or Recuva tools can be helpful in recovering some of your encrypted files. Also, utilities developed by decryption experts may hold the key. Emisoft has a decryption tool specifically for Djvu/Stop Ransomware families, which could work to unlock your encrypted files. However, it only works if offline keys were used to encrypt your files during infection.
Remember, amidst the sophistication of contemporary cyber-attacks, staying ahead requires more than mere reactionary maneuvers. Keep abreast with the evolving cyber threats, maintain an up-to-date antivirus, enforce a stringent backup strategy, and uphold a healthy skepticism towards dubious downloads or too-good-to-be-true online offers.
While handling ransomware such as ITQW cleanup can be daunting, well-rounded knowledge coupled with proactive behavior acts as deterrents. Products and techniques outlined exist to assist you, however, the road to a more secure cyber-world remains a shared responsibility. Forge ahead tech-savvies, enjoy the digital space, but never let down your guard. It’s always better to outsmart the malware than to combat it.
Final Thoughts
Through the deep understanding of how to detect, isolate and subsequently remove ITQW Ransomware from our systems, we arm ourselves with the necessary knowledge to combat this cyber threat. Recovery after such an attack may seem daunting, but with the right tools and approach, it can be effectively managed.
Equipped with this extensive knowledge, we are in a stronger position to secure our systems going forward, effectively setting up a robust defense against future infections. In the quest to keep up with the vigilance needed in this cyber age, constant learning and updating skills is our most potent weapon. Think, learn, and protect – the mantra to safe survive in our cyber-enthralled lives.

Nishant Verma is a senior web developer who love to share his knowledge about Linux, SysAdmin, and more other web handlers. Currently, he loves to write as content contributor for ServoNode and also collaborated with MRLabs now.






























